ransomware
Ransom means ransom or release. Ransomware are ransomware programs that are sent as malwareattached to emails and infect programs, boot sectors or files, encrypt them and put the computer out of service. Ransomware is also known as crypto- virus, crypto-Trojan or crypto-worm.
There are different ransomware approaches with which the ransom is extorted. For example, a victim infected with ransomware cannot open files anymore. He receives an email demanding a ransom. In exchange, he would send a private key with which the ransomware can be removed. If the demand is not met, then the data would be lost.
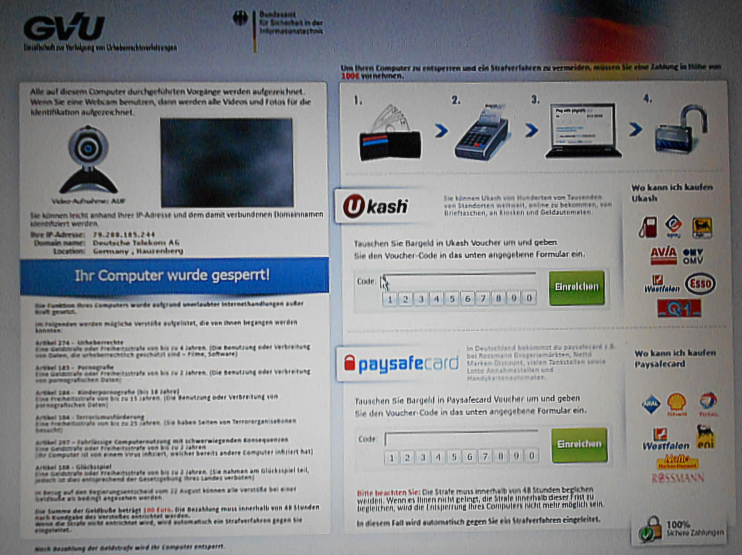
In another scenario, the victim is made to believe that he is involved in police investigations and that there is unlicensed software or illegal websites on his computer. The victim is instructed to transfer a certain amount using e-money or a cryptocurrency. Regardless of the demand approach, the blockade of the computer is not removed and no private key is transferred.
Examples of ransomware Trojans
Examples of such ransomware Trojans are the Bundestrojan and the Cryptolocker. While the Bundestrojan belongs to the boot viruses and gets stuck in the Master Boot Record( MBR) so that the operating system can no longer be started, the Cryptolocker encrypts files using RSA encryption. Both have in common that they display their demands for ransom on the screen.
In the case of the Federal Trojan, the ransomware makes little sense. The cyber criminals have no way to remove the Trojan at all, so the Cryptolocker criminals might send the key to decrypt the files. The user can use the key to decrypt and use the files again.
The recovery after the ransomware
Ransomware recovery is the resumption of PC operations after a ransomware attack, where the attacker encrypts the victim's data and demands a financial payment for the decryption key. Short-term recovery time is an important aspect of recovery, as the cost of downtime can be enormous, and the company's image can also be severely affected. For this reason, it is recommended to create backup copies according to the 3-2-1 rule.