encryption method
There are several procedures for encryptingdata, which are used depending on the application, for example in data transmission. The elementary procedures are based on substitution and transposition.
In the substitution cipher, characters are recoded according to a character list, with characters being replaced by other characters. In the case of the transposition cipher, the letters of a plaintext are rearranged according to a certain scheme, i.e. the sequence of the characters is changed. In the simplest case, this can be done by capturing a text not in lines, but in columns. The algorithm can be run through in several rounds, with each run applying a different working key for control, which is selected from the actual key using a specific function.
Basically, there are two encryption methods: Symmetric encryption and asymmetric encryption, and as a combination of these, hybrid encryption.
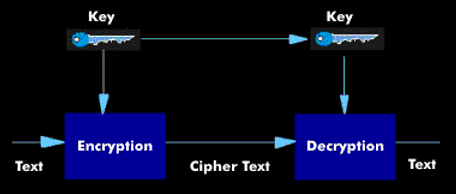
Symmetric encry ption works with a cipher key and a decryption key, which can be easily derived from each other. Symmetric encryption methods include the DES algorithm, 3DES, International Data Encryption Algorithm( IDEA), Blowfish, Kerberos, RC2, RC4 and RC5.
The asymmetrical coding uses two to each other matching asymmetrical keys, whereby between the publicly accessible cipher key(Public key procedure) and the secret personal Dechiffrierschlüssel(Private key procedure) one differentiates. There is no relationship between the two keys, the public key and the private key, so that it is not possible to derive the other key from the one. Asymmetric encryption methods include the RSA method, S/ MIME, the Diffie-Hellman algorithm( DHA) and the PGP algorithm, Pretty Good Privacy (PGP).
Hybrid encryption combines the advantages of both encryption methods. Thus, hybrid encryption uses the symmetric method for message exchange and the asymmetric encryption for key exchange.

.png)