cyber security (CS)
As the world's largest network, the Internet offers attackers ample opportunities to gain unauthorized access to databases and resources, and to manipulate and sabotage databases and transmitted data.
The technical possibilities for unauthorized intrusion into other people's databases range from eavesdropping on passwords, IP spoofing or DNS attacks in which the intruder uses a forged IP address, IP hijacking in which the attacker takes over an existing IP connection, the replay attack, SYN flooding, a targeted attack on theserver to distract it from its actual tasks by overloading it, to the man-in-the-middle attack, an attack in which communication between two partners is intercepted and manipulated.
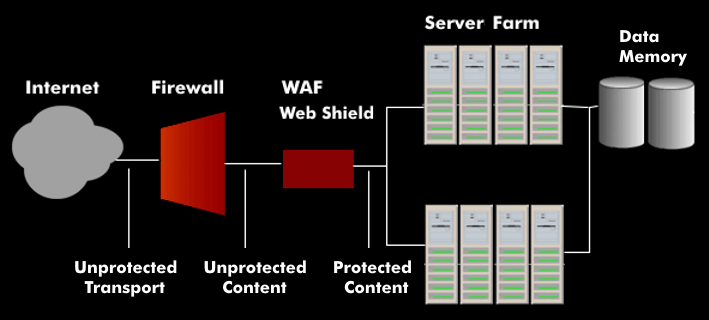
Effective measures against these threats to Internet security or cyber security are provided by web shields that act as an application layer gateway( ALG), also known as a web application firewall(WAF). Unlike classic firewalls and intrusion detection systems( IDS), web shields examine communication at the application layer.